Meta Edits: Your Guide to Short-Form Video Editing
Meta recently launched Edits, a mobile-only video editing tool built into Instagram and Facebook. This app comes with AI-powered templates, timeline editing, automatic captions, green-screen effects, and a royalty-free audio library .
Moreover, Edits offers seamless sharing to Reels and other platforms without watermarks . It’s also free and doesn’t require a subscription unlike CapCut imusician.pro
However, Edits lacks some advanced tools—like keyframes and expansive music libraries—that CapCut currently offers . Still, Meta plans to integrate features like teleprompter mode, collaboration tools, and AI-based styling in upcoming updates
In short, Edits positions Meta as a robust player in the short-form video space—particularly if CapCut faces U.S. regulatory headwinds .
Getting Started with Meta Edits
First, download the standalone Edits app from the iOS App Store or Google Play. Then, log in using your Instagram account. This tight integration with Meta platforms ensures seamless sharing to Reels and Facebook posts
Next, open Edits and explore the five main tabs: Ideas, Inspiration, Projects, Record, and Insights. Here’s what you’ll find:
- Ideas: store video concepts.
- Inspiration: browse trending audio and formats.
- Projects: import clips or review drafts.
- Record: film up to 10‑minute vertical videos.
- Insights: check engagement metrics after posting
Then, create or import your video. Next, use simple prompts to edit automatically with AI, or fine‑tune with frame‑accurate timeline tools. Additionally, add transitions, green‑screen effects, auto‑captions, and royalty‑free audio—with no watermarks upon export
Finally, export in HD, 2K, or 4K, and share directly to Instagram or Facebook. Also, you can save the video elsewhere without any branding .
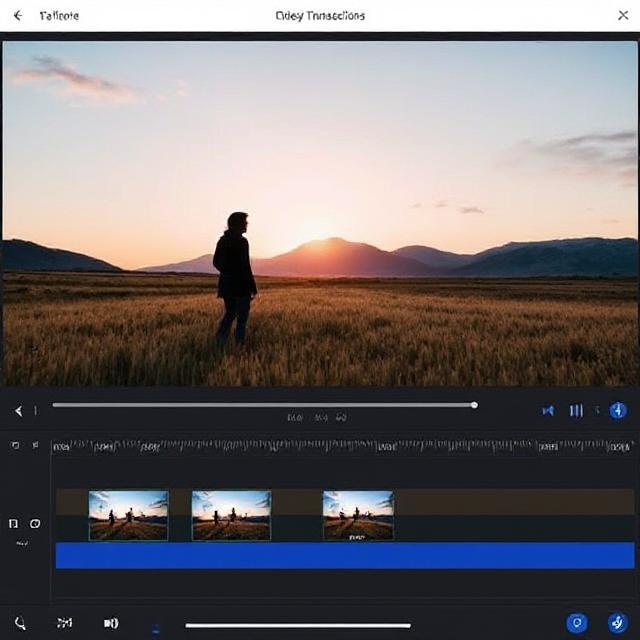
Key Features of Meta Edits
- Video Trimming: Precisely cut and trim your video clips to the desired length.
- Text Overlays: Add stylish text overlays to enhance your video content.
- Filters and Effects: Choose from a variety of filters and effects to give your videos a unique look.
- Music Integration: Incorporate background music from a built-in library or upload your own audio tracks.
- Transitions: Seamlessly blend different video clips together using smooth transitions.
Step-by-Step Guide to Editing Videos
- Import Your Video: Start by importing the video clip you want to edit into Meta Edits.
- Trim the Video: Use the trimming tool to cut unnecessary parts of the video.
- Add Text Overlays: Incorporate text to convey important messages or add context.
- Apply Filters and Effects: Choose filters and effects to enhance the visual appeal of your video.
- Incorporate Music: Add background music to make your video more engaging.
- Add Transitions: Blend different clips using transitions for a seamless viewing experience.
- Preview and Export: Preview your edited video and export it in the desired resolution.
Tips for Creating Engaging Short-Form Videos
- Keep it Short: Aim for videos that are concise and to the point.
- Use Captions: Add captions to ensure your video is accessible to everyone.
- Engage with Trends: Participate in popular trends to increase visibility.
- Optimize for Mobile: Ensure your video is optimized for mobile viewing.
- Use High-Quality Visuals: Use high-resolution video clips to maintain viewer engagement.












